Where Kontron Mission Computers Deliver Tactical Advantage
Kontron rugged computing platforms power a wide range of mission-critical systems—from unmanned vehicles
to airborne ISR and C4ISR command posts.
Each solution is built on proven Kontron building blocks, ensuring performance, security, and long-term program reliability.

High-performance computing for radar processing, imaging, secure communications, mission management.
Ideal for ISR missions, situational awareness, and advanced airborne systems.
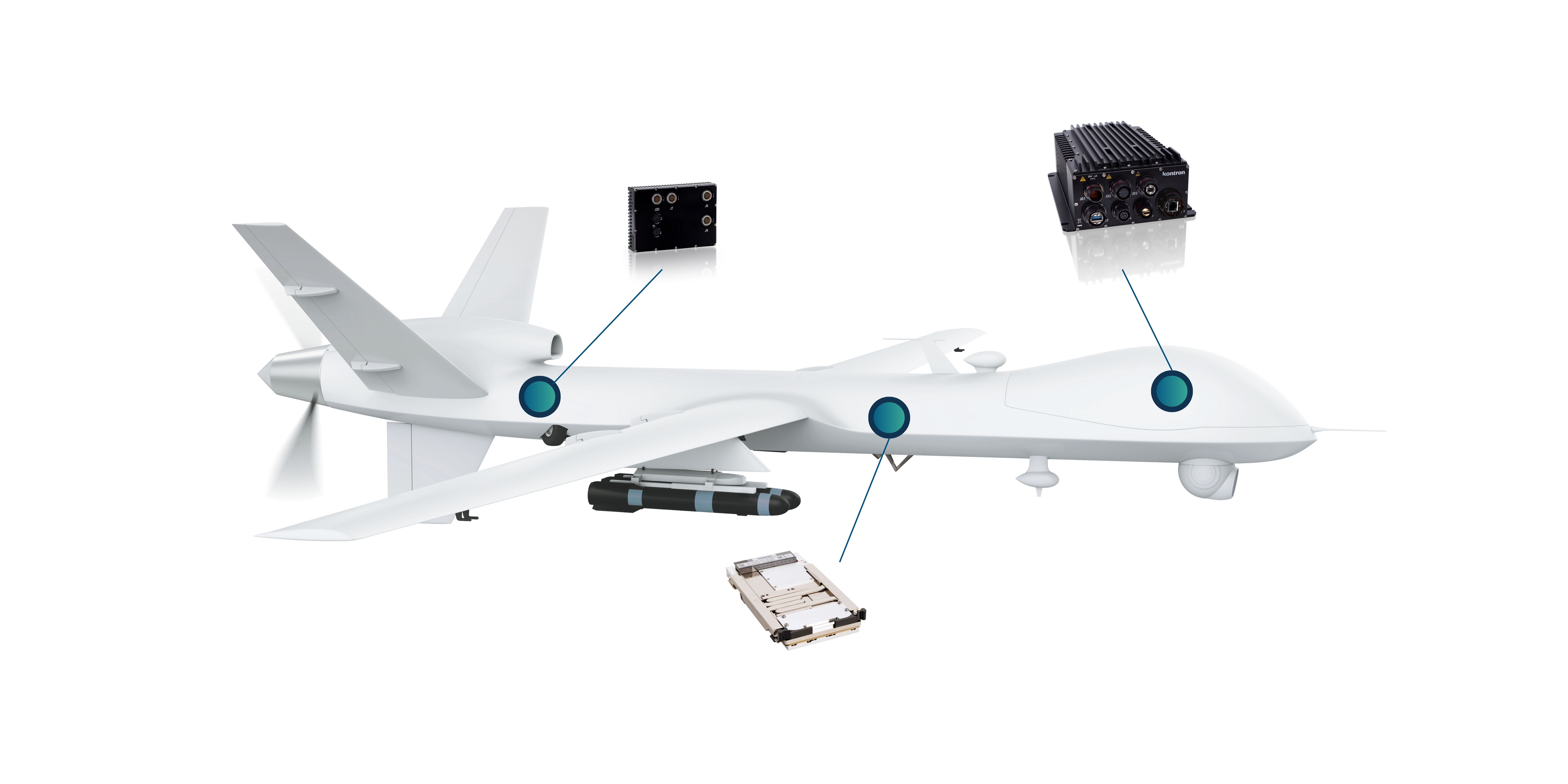
Rugged low-SWaP mission computers for onboard AI, sensor fusion, and autonomous aerial operations.
Ideal for ISR payloads, target tracking, and real-time intelligence processing.

MIL-STD mission systems enabling C4ISR, vetronics integration and real-time situational awareness.
Designed for armored vehicles, reconnaissance platforms, and mobile mission systems.

Rugged MIL-STD computing for airborne ISR, sensor fusion, and secure mission avionics.
Ideal for multirole helicopters, surveillance rotorcraft and advanced mission management systems.
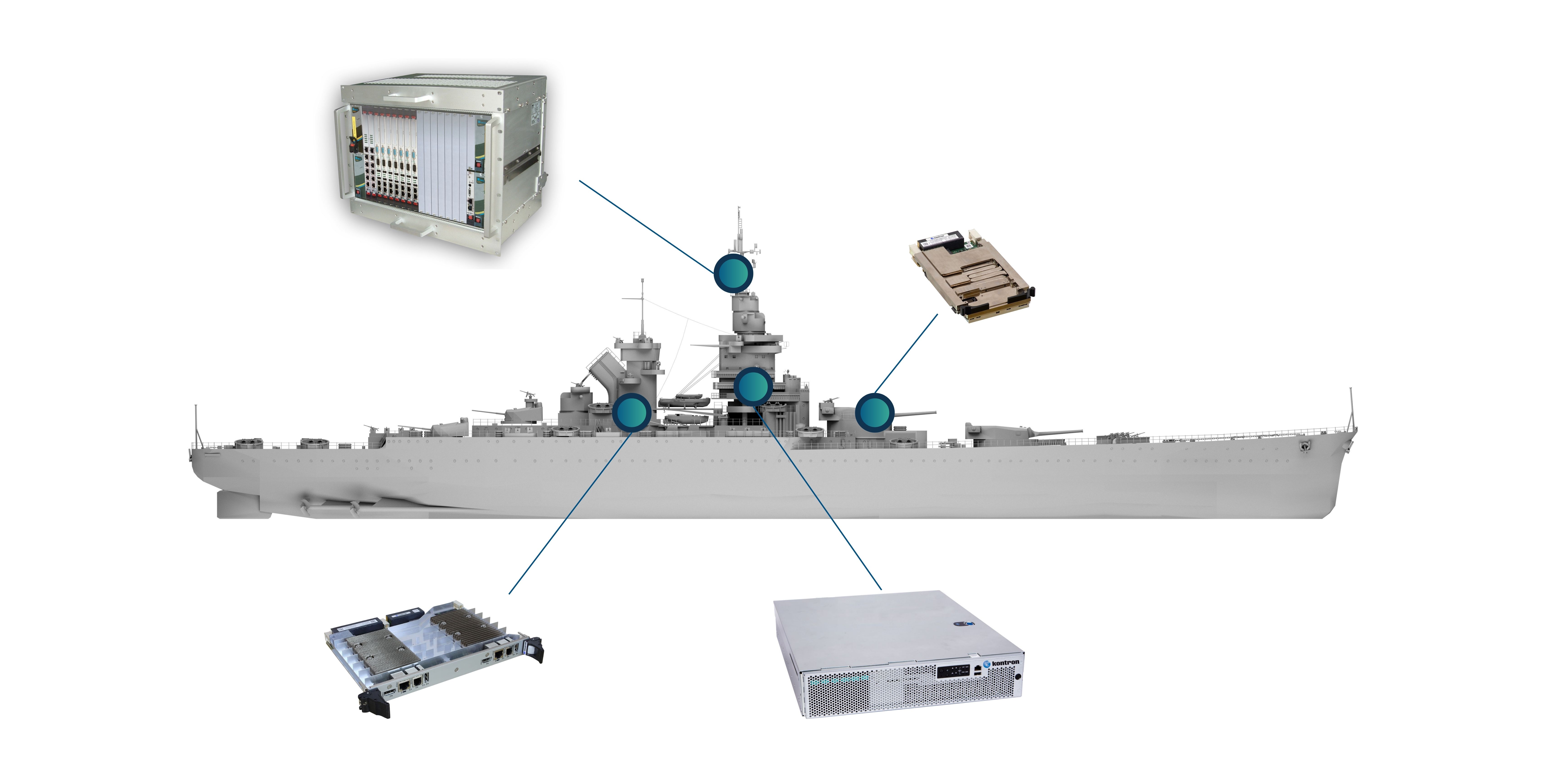
Rugged, secure systems for sensor integration, command and control, navigation, and onboard data processing.
Optimized for shipborne ISR, surveillance functions, and real-time maritime operations.