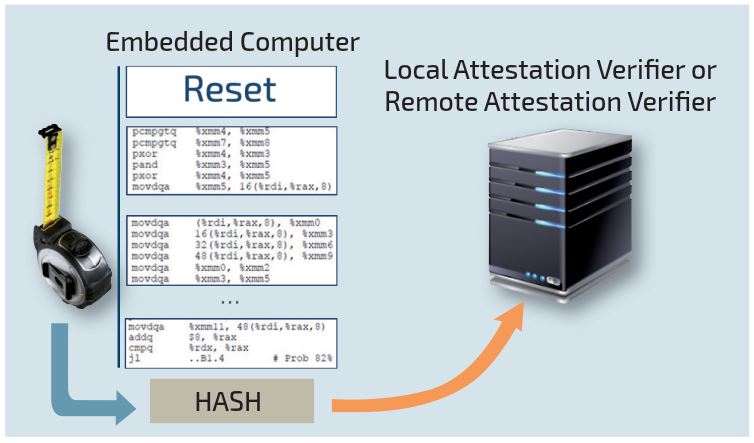
Trusted Boot
Protecting the system software during the boot with TPM Secure Element
The trusted boot mechanism relies on the TCG (Trusted Computing Group) international standard, where a Trusted Platform Module (TPM) secure element is used to verify the
validity of the boot of a computer. The TPM measures through a hash value all pieces of code executed during the boot, including firmware, firmware setup, bootloader, operating system and
more if needed. Any single bit change in the boot, as compared to a reference value, can be detected and reported in a local or remote cryptographic attestation. In case of unexpected hash of the boot code, the device is disconnected. Remote update of the device can still happen to restore correct operation.
Kontron x86 computers equipped with TPM secure element and running Linux can offer Trusted Boot service.
For a guided demo, please contact us through the form Request Live Presentation.
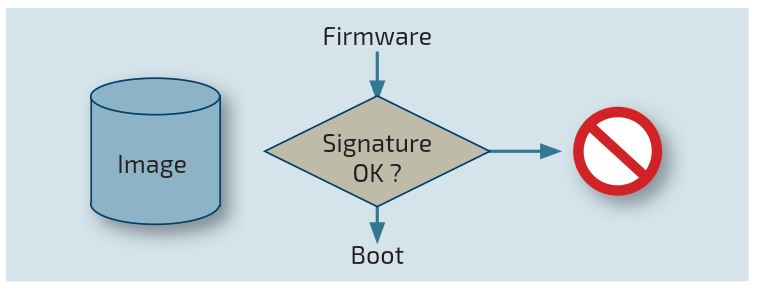
Secure Boot
Booting only signed software from the BIOS firmware
The purpose of the secure boot is to make an embedded computer restricted to boot from the firmware only authentic code, typically from a disk or SSD. The secure boot mechanism is a purely software security strategy at the BIOS level to prevent booting of a binary which is not properly signed. With this security in place which is protected by the BIOS passsword, no one can boot a software which is not explicitly listed as authorized. The list of allowed signatures is stored in the BIOS firmware as a set of certificates and can be updated from a BIOS configuration menu.
Keys needed to activate the secure boot are:
- PK Plateform Key: key of the hardware platform needed to verify the KEK keys.
- KEK Key Exchange Keys: key(s) of the owner(s) of the software to boot.
- DB key(s): key(s) of the different software image or version of software allowed to boot. Used to verify the signature(s) of the software to boot.
- DBX key(s): key(s) of software or version of software explicitely prohibited to be booted.
The secure boot service is available on Kontron x86 CPU boards running a UEFI BIOS firmware.
Authentication with TPM
Authenticating system hardware during SSL/TLS secure communication with TPM Secure Element
Establishing a secure network connection
A private key is needed on the server side at least, and also recommended on the client side for embedded computing since no operator is present to enter a password. It is often NOT a good idea to store the private key on the disk, even encrypted, because at some point, it will be decrypted in memory and CPU registers when used at the beginning of a network session.
Using and storing the private key with TPM authentication
TPM authentication is providing a hardware protection to private keys. This hardware protection prevents the private key from being stolen, and thus avoids a potential duplication of a compromised server or client machine, or a man in the middle strategy spying the communication.
Approtect
Protecting application integrity and confidentiality with hardware secure element
Main security threats at the application level:
Integrity
The running application might be hacked or patched in binary, on the disk or in memory, to modify its behavior or work around some checks.Confidentiality
The way the application code is working could be analyzed in details by looking at the execution code, in order to learn or to reproduce its behavior.Unauthorized copies
The embedded systems (software application or full equipment) suffer the risk of being cloned without authorization.
The APPROTECT solution, using a security technology from Wibu, a Kontron partner, protects the application from those risks with the security of a dedicated hardware secure element located on all Kontron boards. All or part of the application execution code is encrypted on the storage device and will only be decrypted in memory in presence of the keys stored inside the secure element. At run time, the integrity of the application in memory is also permanently checked. The application can be fully encrypted as a whole with no modification, or only critical part can be encrypted by using a dedicated API.
Software Vulnerability Watch
Being informed of sowtware vulnerabilities affecting configurations in the field and getting fixes when available
With long life cycles and complex supply chains, embedded computers are especially exposed to malware attacks targeting older versions of OS distributions and silicon microcode. Kontron Software Vulnerability Watch service allows customers to share the burden of monitoring published vulnerabilities, establishing the exposure level for already deployed equipment and providing the necessary fix.
Kontron Software Vulnerability Watch service
It typically consists, for the Linux operating system environment, in defining the software bill of material, in monitoring the published vulnerabilities impacting the configuration, and when available from the software editor, in packaging and distributing the corresponding software fix.
DISTRIBUTED SECURITY WITH COTS CPU BOARDS
Highly sensitive Embedded Applications can benefit from secure elements available on COTS CPU Boards to build a robust digital security solution. Distributing a secret in different circuits significantly lowers the risk of a successful attack, reduces the impact of the discovery of vulnerability and streamlines the security rules associated with the provisioning of the keys.
Discover how standard hardware security mechanisms on COTS CPU boards can be leveraged to build a distributed security scheme with critical keys stored in distinct secure elements.
Read the application note