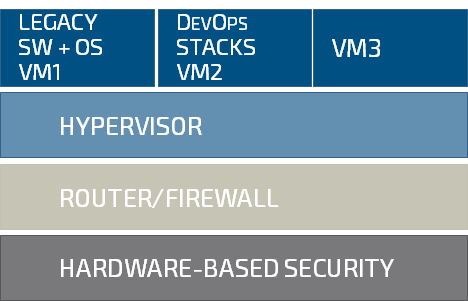
SEC-Line features and benefits
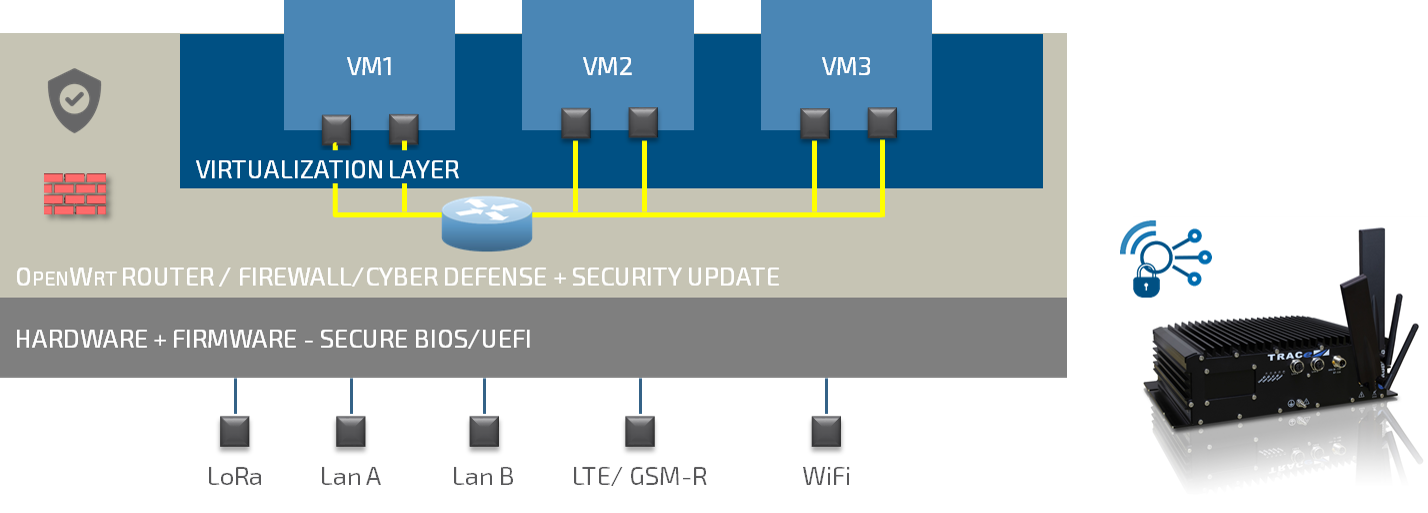
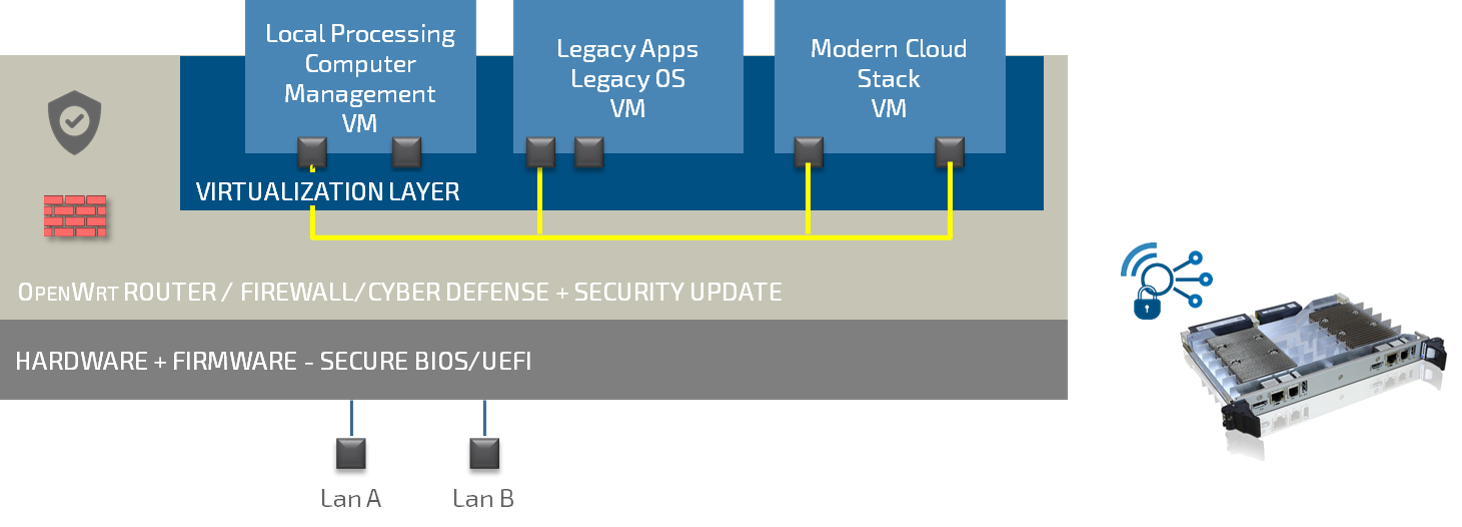
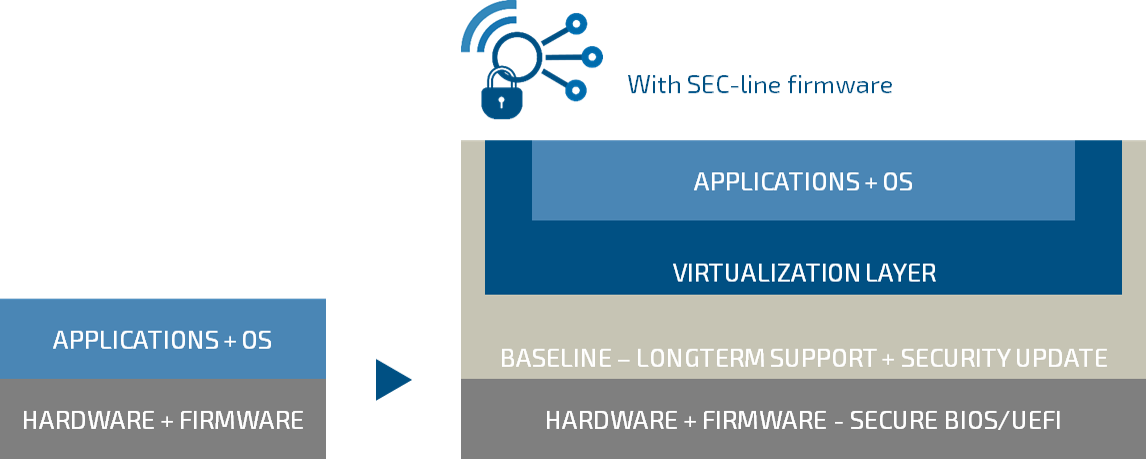
Embedded Computing becomes Edge Computing

-
Agility
OS and Cloud agnostic, Legacy and DevOps friendly
-
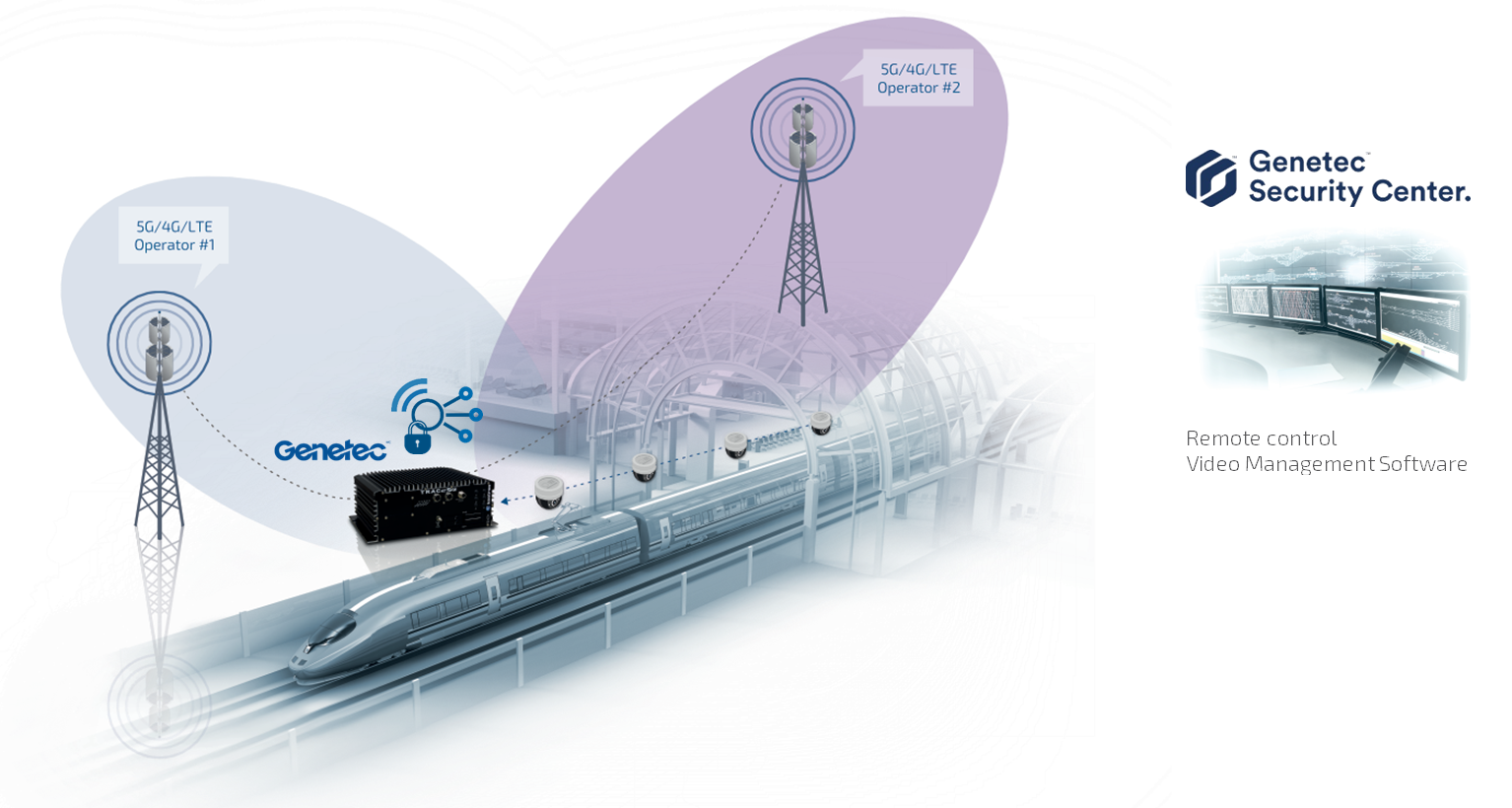
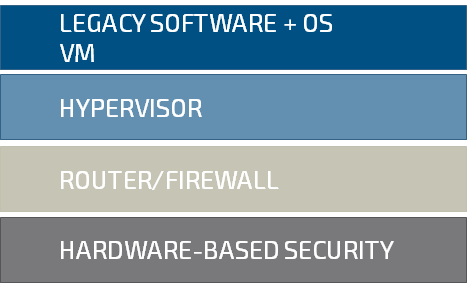
Connectivity
Leading egde router/firewall, central management
-
Security
HW root of trust, Encrypted updates, Remote Attestation, Cyber defense
-
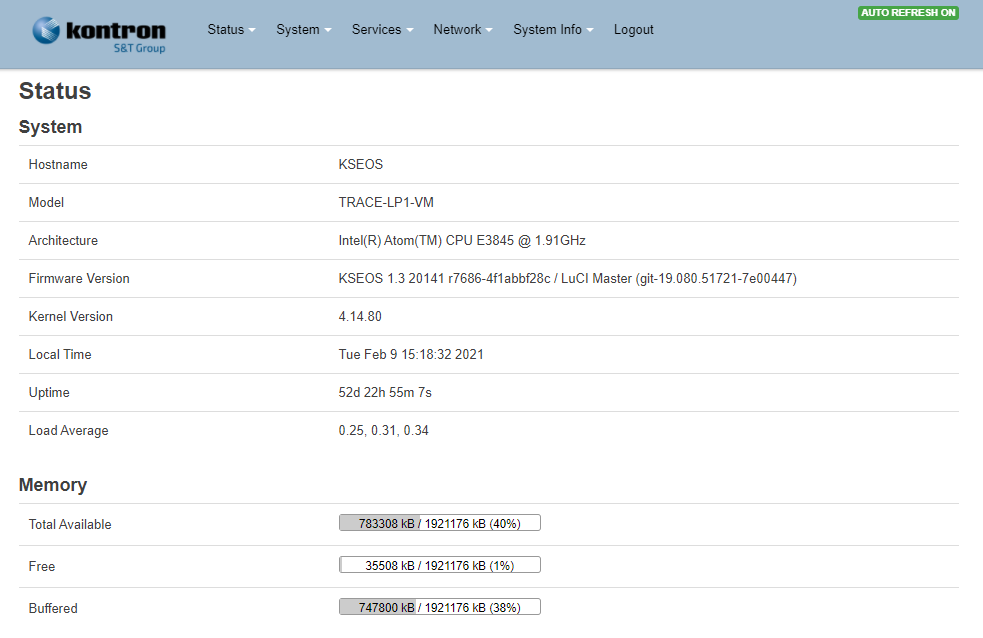
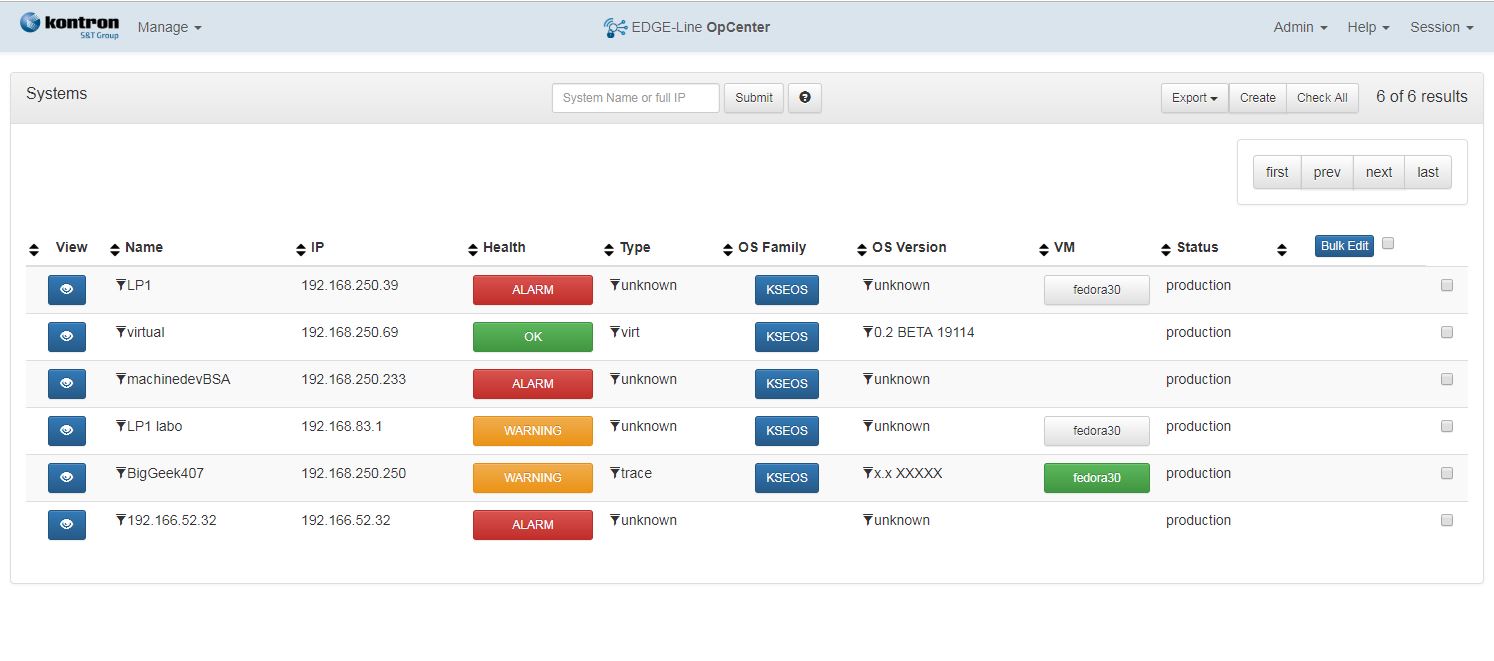
Manageability
Unique control point, Central database Store OS updates, OS Settings, VM Images, System information